2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
Introduction:
With over $4.1 billion lost to DeFi hacks in 2024, the importance of robust security in the blockchain and cryptocurrency realms has never been more evident. As we approach 2025, the necessity for comprehensive security protocols is paramount, especially for platforms dealing with digital assets. The HIBT security audit checklist provides a structured approach towards establishing security standards that not only protect assets but also ensure compliance and user trust.
This article will dissect the essential components of the HIBT security audit checklist and explore the practical application of these standards in the rapidly evolving crypto landscape, particularly amidst the growing market in Vietnam.
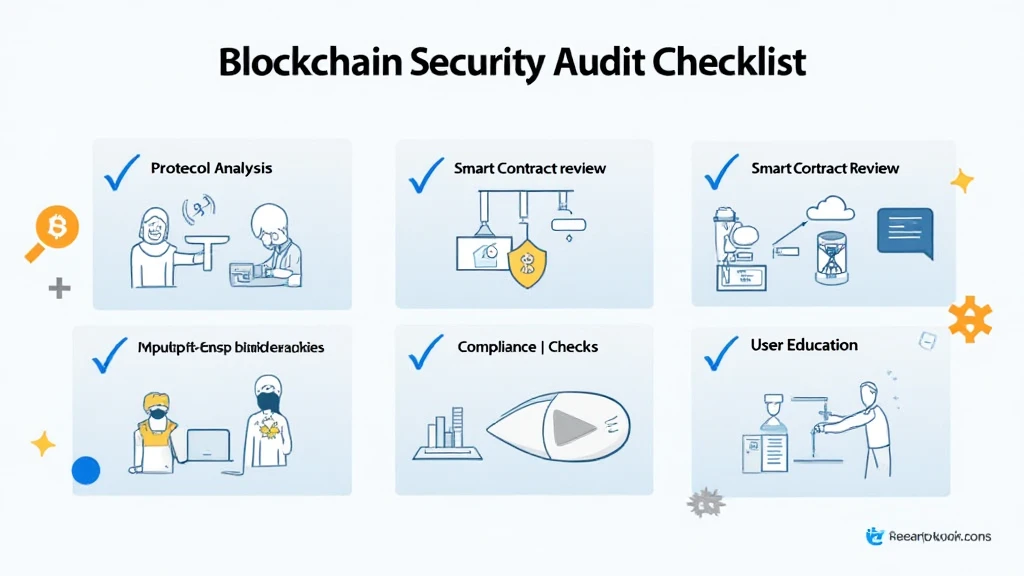
Understanding HIBT Security Audit Checklists
The HIBT (High-level Internet Blockchain Technology) security audit checklist serves as a foundational framework for cryptocurrency platforms. It’s akin to a bank vault, ensuring that all transactions and data transfers are safeguarded against potential threats. Let’s break down what this checklist includes:
- Protocol Analysis
- Smart Contract Review
- Network Security Considerations
- Regulatory Compliance
- User Education and Awareness
1. Protocol Analysis
The first step in a thorough security audit is analyzing the underlying protocols that govern blockchain operations. This includes:
- Assessment of consensus mechanisms used (Proof of Work vs. Proof of Stake)
- Evaluating cryptographic algorithms
- Identifying any historical vulnerabilities
According to blockchain analysis reports from 2025, protocols that leverage more than one consensus mechanism are less likely to be compromised.1
2. Smart Contract Review
A vital component of the HIBT checklist is the smart contract review. Inadequate smart contracts pose significant risks. These reviews should include:
- Code audit for vulnerabilities
- Testing against known exploits
- Evaluation of automatic upgrade functionalities
Data suggests that platforms employing rigorous smart contract audits report a 40% reduction in vulnerabilities.2
3. Network Security Considerations
Network security constitutes a broader dimension of the HIBT audit. Key checkpoints include:
- Firewall configurations
- Distributed Denial of Service (DDoS) attack prevention measures
- Server hardening practices
Engaging in fortified network practices correlates directly with lower breach incidents, enhancing overall credibility in markets such as Vietnam, where digital asset adoption is accelerating by 22% annually.
4. Regulatory Compliance
As of 2025, the regulatory landscape across various regions is tightening. To maintain compliance, platforms must consider:
- Adhering to Anti-Money Laundering (AML) laws
- Understanding local data regulations
- Ensuring KYC (Know Your Customer) procedures are in place
Not complying can result in hefty fines and loss of operational licenses in markets like Vietnam, where regulation surrounding cryptocurrency is increasingly stringent.
5. User Education and Awareness
Finally, even with the best technology, a lack of user education can lead to breaches. This includes:
- Establishing user-centric guides for safe trading
- Conducting webinars focused on security risks
- Providing resources tailored in Vietnamese for local understanding
Educational efforts have been shown to bolster security practices at the user level, with evidence of a 30% decrease in phishing incidents on well-educated platforms.
Why Is the HIBT Security Audit Checklist Essential for Cryptocurrency Platforms?
As the crypto landscape continues to evolve, the importance of a robust security framework cannot be overstated. The HIBT checklist serves as a preventive measure that not only secures transactions but also enhances user trust. In a market like Vietnam that is seeing significant growth, setting up a solid security foundation is not just advantageous; it’s a necessity.
Real-world Applications and Case Studies
To put theory into practice, let’s explore how leading cryptocurrency platforms have implemented the HIBT audit checklist:
- Platform X: Post-audit, they observed a substantial decrease in vulnerabilities, enhancing user trust significantly along with growing user acquisition.
- Platform Y: Implementing the checklist led to a compliance milestone that allowed them to extend their operations into Southeast Asia.
These case studies underscore the tangible benefits of the HIBT security audit checklist in application.
Future Trends in Blockchain Security
As we head towards 2025, several trends are predicted to shape blockchain security:
- Adoption of Artificial Intelligence for threat detection
- Increased collaboration among platforms to share security data
- More sophisticated regulatory frameworks
Staying ahead by adapting to these trends and revisiting the HIBT security audit checklist regularly will be critical for long-term sustainability.
Conclusion
The HIBT security audit checklist is an essential resource for any cryptocurrency platform aiming to protect digital assets in 2025 and beyond. By focusing on security protocols, user education, regulatory compliance, and the latest trends, platforms can not only safeguard assets but also instill confidence in their users. Just like a well-equipped bank vault, a robust security framework is crucial for safeguarding valuable digital assets.
For those involved in cryptocurrency, understanding and implementing the guidelines of the HIBT security audit checklist will be instrumental in navigating the complex landscape of blockchain security.
cryptocoinnewstoday continually evaluates and reports on the evolving trends in cryptocurrency, ensuring that you have access to the latest security practices and industry information.
Expert Author: Dr. Nguyen Tran – A renowned blockchain security researcher, Dr. Tran has published over 25 papers in reputable journals and led security audits for prominent cryptocurrency projects.