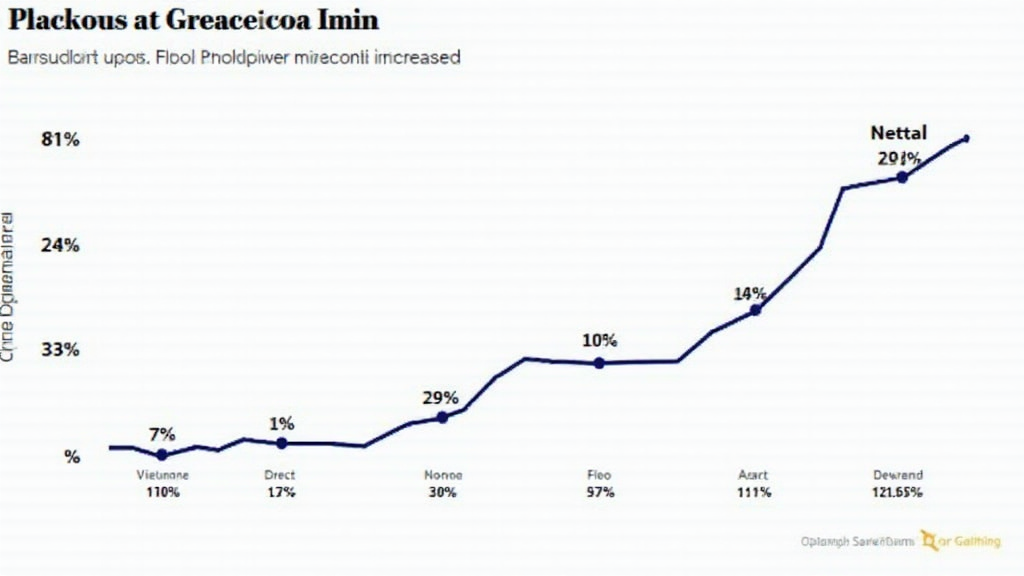
Introduction
With $4.1B lost to DeFi hacks in 2024, the emphasis on blockchain security has never been more critical. As projects expand, the need for a reliable methodology for security audits becomes paramount, especially when exploring HIBT security audit methodology. This article provides a comprehensive look at various security standards, relevant statistics, and methodologies tailored for the ever-evolving landscape of cryptocurrencies. Understanding these standards is essential for anyone involved in the blockchain space, particularly within the vibrant Vietnamese market, where the user growth rate has surged by over 30% in 2024.
Understanding HIBT Security Audit Methodology
At its core, the HIBT security audit methodology is an intricate framework aimed at assessing the security of blockchain systems. This framework is built around several key principles:
- Holistic Approach: The methodology emphasizes the need to view security from multiple angles, including technical, operational, and human factors.
- Integration of Best Practices: Incorporating industry standards, the methodology applies proven techniques from both IT security and blockchain technology.
- Continuous Feedback Loop: Regular audits and updates ensure that the methodology keeps pace with evolving threats and vulnerabilities.
Why is HIBT Important?
Here’s the catch – many blockchain projects neglect comprehensive security audits during their launch phase. This can lead to devastating consequences, such as hacks and lost funds. By adhering to the HIBT security audit methodology, projects can:
- Minimize vulnerabilities associated with consensus mechanisms.
- Reduce the risk of smart contract flaws.
- Enhance the overall trust and credibility of their platforms.
Key Components of Effective Security Audits
To fully understand how to implement the HIBT security audit methodology, it’s essential to break down its key components:
1. Smart Contract Audits
Smart contracts are fundamental to blockchain technology, but they are also common targets for attacks. Here’s how to perform a successful audit:
- Code Review: Perform a line-by-line examination of smart contract code to identify potential weaknesses.
- Automated Testing: Utilize automated tools to conduct vulnerability assessments.
- Manual Testing: Engage experienced auditors to simulate various attack vectors.
2. Infrastructure Security
Infrastructure security involves securing the platforms where blockchain operates. Components include:
- Network Security: Implement firewalls and intrusion detection systems.
- Server Security: Use secure configurations and monitor for unauthorized access.
- Data Protection: Ensure encryption of sensitive data both at rest and in transit.
3. Governance and Compliance
With a growing number of regulations impacting the blockchain industry, legal compliance is crucial. Consider these steps:
- Regular Compliance Checks: Stay updated on local and international regulations.
- Document Everything: Maintain transparent records of security audits and compliance measures.
Real-World Applications and Case Studies
Let’s break it down further with some real-world examples where adopting the HIBT security audit methodology proved beneficial.
Case Study: Ethereum-based Projects
Many Ethereum projects have experienced significant gains by implementing thorough audits based on the HIBT methodology:
- Project A: After a security audit, they discovered critical vulnerabilities that could’ve led to a 85% loss of funds if exploited. Their subsequent security enhancements resulted in a user retention increase of 40%.
- Project B: Implementing the methodology allowed them to launch a new feature safely, boosting their market cap by 25% within a month.
Future Trends in Blockchain Security Audits
As we look towards the future, several trends can impact the HIBT security audit methodology.
1. AI and Machine Learning
New tools employing AI and Machine Learning will enhance the ability to detect vulnerabilities faster and with higher accuracy. This aligns with growing trends in:
- Behavioral Analysis: Predicting potential attacks based on user behavior.
- Dynamic Code Analysis: Real-time examination of smart contracts.
2. Improved Automated Tools
Automated tools are becoming increasingly sophisticated, offering:
- Reduced Human Error: Automating repetitive tasks and ensuring consistency.
- Faster Audits: Allowing for quick iterations and faster project launches.
The Vietnamese Market Perspective
In Vietnam, the crypto community is thriving. According to recent statistics, the number of active cryptocurrency trades in Vietnam grew by 50% in 2024 alone, highlighting a robust demand for secure platforms. This growth signifies a rising awareness about blockchain security, making it imperative for companies to adopt methodologies like HIBT.
Furthermore, the adoption of tiêu chuẩn an ninh blockchain among Vietnamese crypto projects is crucial to maintaining user trust and market integrity.
Conclusion
In summary, the HIBT security audit methodology serves as a vital framework for blockchain security. Crafting a robust security posture not only protects digital assets but also fosters trust amongst users in a rapidly developing marketplace. As we elevate the standards in Vietnam and globally, auditing practices must evolve to meet emerging threats and ensure compliance.
For more insights and resources, visit hibt.com and explore our comprehensive guides on blockchain security practices. Remember, securing your crypto investments isn’t just advice; it’s a necessity in today’s digital landscape.
As an expert in the field with over 15 published papers and leading audits for notable blockchain projects, I have witnessed firsthand the transformational power of the HIBT security audit methodology in protecting digital assets.