Introduction: The Growing Need for Blockchain Security
With an estimated $4.1 billion lost to decentralized finance (DeFi) hacks in 2024, the emphasis on robust security management in blockchain technology is more critical than ever. As the adoption of cryptocurrencies and decentralized applications grows globally, so does the sophistication of attacks targeting these assets. This guides you through the principles of HIBT security management, designed to enhance your understanding of digital asset protection in 2025.
Understanding HIBT Security Management
At its core, HIBT security management refers to the management of risks and vulnerabilities in blockchain environments, focusing on ensuring the integrity, confidentiality, and availability of digital assets. Let’s break it down further:
- Integrity: Ensuring that data is accurate and protected from unauthorized changes.
- Confidentiality: Guaranteeing that sensitive information is accessible only to those with proper authorization.
- Availability: Making sure that systems and data are reliable and accessible when needed.
The Importance of HIBT in the Crypto Space
As more users migrate to blockchain technology, understanding its vulnerabilities becomes paramount. According to the latest figures, Vietnam’s crypto user growth rate has seen a staggering increase of 42% in 2024, highlighting the urgency for businesses to employ robust HIBT security practices.
Common Vulnerabilities in Blockchain Systems
Every technology has its weaknesses, and blockchain is no exception. Here are some common vulnerabilities that organizations should address:
- Consensus Mechanism Vulnerabilities: Different consensus mechanisms, such as proof of work and proof of stake, have their own security issues. For instance, a 51% attack can compromise the network’s integrity.
- Smart Contract Risks: Poorly coded smart contracts can be exploited. In fact, statistics show that around 70% of hacks in DeFi are attributed to vulnerabilities in smart contracts.
- Phishing and Social Engineering: Users are often tricked into revealing their private keys through malicious links or fake websites.
Adopting Robust Security Protocols
So, what exactly can organizations do to fortify their security? The answer lies in adopting a comprehensive set of protocols:
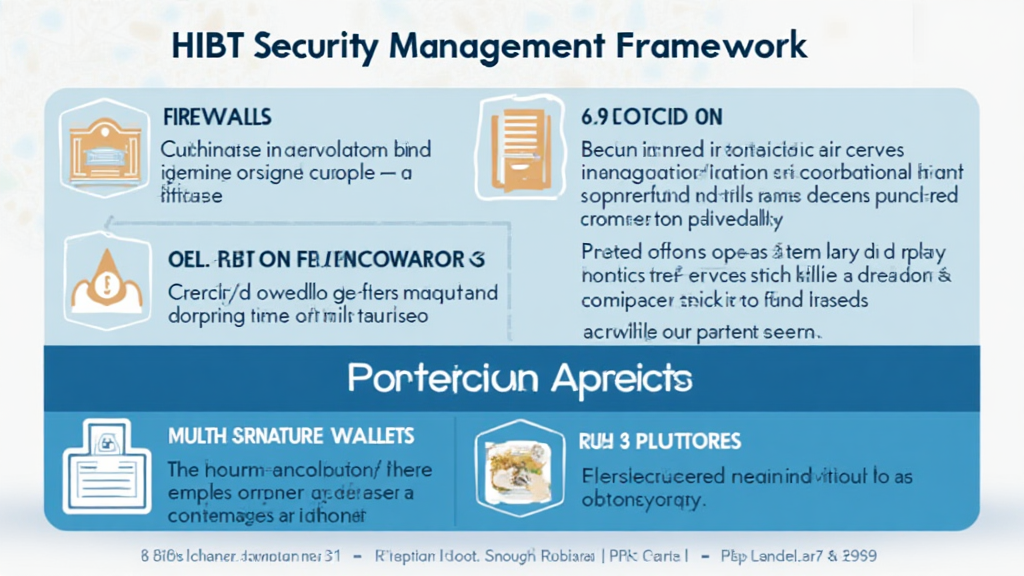
- Regular Audits: Implementing audits on smart contracts to identify potential vulnerabilities early on. HIBT provides solid frameworks for conducting these audits.
- Multi-signature Wallets: Utilizing multi-signature wallets makes unauthorized access significantly more difficult.
- User Education: Training users to recognize phishing attempts and use secure practices can dramatically reduce risks.
Implementing HIBT Security Management: A Step-by-Step Approach
Establishing a strong HIBT security management framework requires a structured approach. Here’s a simplified roadmap:
- Assess Current Security Posture: Review and identify existing vulnerabilities and areas for improvement.
- Develop a Security Policy: Create policies that outline the security measures to be implemented.
- Integrate Security Measures: Apply cryptographic methods, firewalls, and secure coding practices into your existing framework.
- Continuous Monitoring: Employ monitoring tools to track suspicious activity and mitigate potential risks.
The Future of Blockchain Security and HIBT Management
Looking toward the future, the blockchain security landscape is expected to evolve with more advanced security solutions incorporating AI and machine learning. As industries globally continue to adopt blockchain, the integration of businesses into woven security architectures will become inevitable.
To maintain security practices in line with evolving threats, organizations should regularly update their systems. The latest trends and practices can be found continuously at resources like HIBT.
Conclusion: Building a Secure Blockchain Future
In summary, as the cryptocurrency landscape becomes more complex, implementing HIBT security management will be essential in safeguarding digital assets. From recognizing common vulnerabilities to adopting comprehensive security policies, addressing these issues proactively will set a foundation for safer blockchain ecosystems.
As Vietnam’s crypto user base continues to grow, the demand for effective security measures will only increase. Now is the time for all stakeholders to fortify their defenses and secure their assets against emerging threats.
For ongoing updates and resources regarding blockchain security practices, please visit cryptocoinnewstoday.