Introduction
As the cryptocurrency landscape continues to evolve, Vietnam stands out with a rapidly growing market for digital assets. According to recent statistics, the country has seen a 220% increase in crypto users from 2021 to 2023. With $4.1 billion lost to DeFi hacks in 2024, ensuring robust security measures has become crucial for users and platforms alike.
This article explores various Vietnam crypto 2FA methods that hold the potential to secure your digital assets. Our goal is to provide comprehensive insights and actionable steps, making your journey in the crypto space safer and more informed.
Understanding 2FA and Its Importance in Vietnam’s Crypto Market
Two-Factor Authentication (2FA) acts as a critical layer of security for online accounts, particularly for those managing cryptocurrencies. In a landscape characterized by the illicit siphoning of funds, integrating 2FA can dramatically reduce your risk of being targeted for hacks.
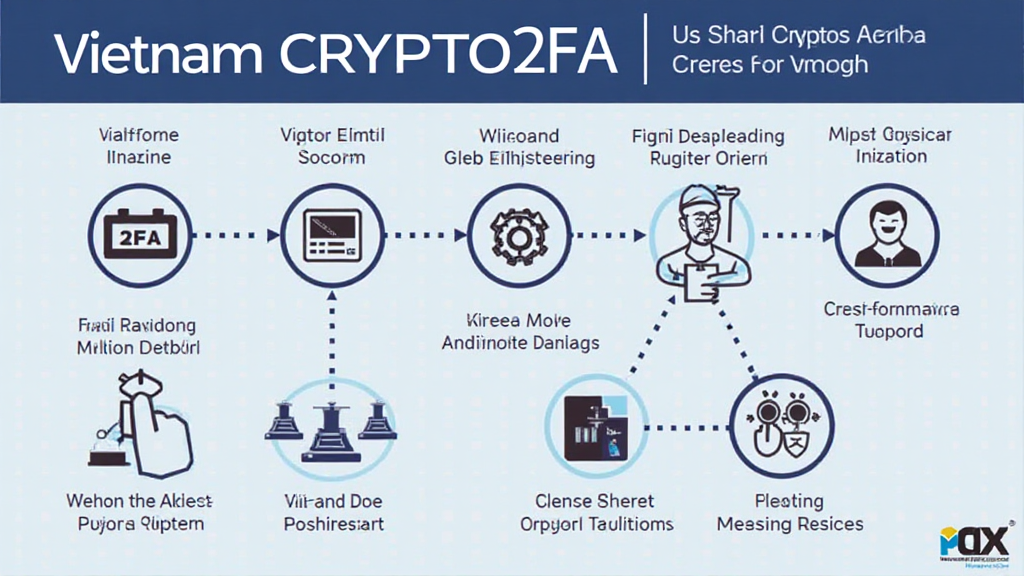
- What is 2FA? 2FA requires users to provide two different forms of identification before accessing their accounts—typically something you know (password) and something you have (a device).
- The Rise of Crypto in Vietnam: The increasing interest in cryptocurrencies has made Vietnam a target for hackers, thus emphasizing the need for robust security practices.
Common 2FA Methods in Vietnam
Vietnamese crypto users have several options when it comes to implementing 2FA. Each method presents its own advantages and potential drawbacks. Here are a few common methods:
1. SMS-Based Verification
This method sends a verification code to your registered mobile phone number. While convenient, it’s essential to be cautious due to risks associated with SIM swapping attacks.
2. Authentication Apps
Apps like Google Authenticator or Authy generate time-sensitive codes that add an extra layer of security. These applications work offline, which makes them less vulnerable to communication-based attacks.
3. Hardware Tokens
A physical device that generates a code which must be entered during the login process. Examples include YubiKey or Ledger Nano S. These devices are considered among the most secure options due to their offline nature.
Choosing the Right 2FA Method for You
When selecting a 2FA method, consider:
- Ease of use
- Security level
- Compatibility with the crypto platform you are using
For instance, an increasing number of platforms in Vietnam, like hibt.com, advocate using authentication apps to enhance user security.
Challenges and Concerns of 2FA in Vietnam
While 2FA significantly mitigates risks, it is not foolproof. Users must remain vigilant about:
- Phishing Attacks: Be wary of unsolicited messages asking for verification codes.
- Device Security: Ensure your phone or hardware device is secure and not compromised.
Future Trends: The Evolution of 2FA Techniques
As technology progresses, alternative methods may emerge. Some trends to watch in Vietnam’s crypto landscape include:
- Biometric Authentication: Fingerprint and facial recognition could eventually offer a seamless security experience.
- Decentralized Identity Solutions: Potentially revolutionizing how identity verification works, making it more secure and easier to manage.
Conclusion
As we’ve seen, securing your cryptocurrency against theft and hacks in Vietnam requires a multi-faceted approach. By implementing one or more Vietnam crypto 2FA methods, you can bolster your defense against potential attacks.
In conclusion, always remain aware of the risks associated with crypto investments and continuously review your security strategies.
For more insights and updates, stay connected to cryptocoinnewstoday. Your safety in the digital asset domain matters.
Author: Dr. Nguyen Minh, a renowned blockchain security researcher with over 15 published papers in the field, specializes in auditing smart contracts for reputable projects. He is committed to educating users about safe cryptocurrency practices.