Introduction
With $4.1 billion lost to DeFi hacks in 2024, the need for robust security standards in the cryptocurrency sector has never been more urgent. Investors and operators alike are waking up to the critical importance of comprehensive compliance measures. This is where the HIBT crypto security compliance checklist comes into play, serving as an essential tool for any cryptocurrency platform aiming to protect digital assets and secure user trust.
In this article, we’ll delve deep into what makes a successful security compliance plan, emphasizing the importance of adhering to standards that meet regulatory expectations in dynamic markets like Vietnam, where user adoption is growing exponentially.
The Importance of the HIBT Compliance Checklist
The HIBT (Highly Important Blockchain Trust) compliance checklist is tailored for crypto platforms to ensure they meet security protocols effectively. Think of it as a safety net—similar to how a bank vault protects physical currency, the HIBT checklist guards against vulnerabilities in digital asset management.
- Understanding Risks: It’s crucial to identify potential threats, from hacks to insider fraud.
- Regulatory Framework: Adhering to compliance helps avoid penalties and enhances platform credibility.
- Building User Trust: Transparency in security measures strengthens user loyalty and engagement.
Key Components of the HIBT Crypto Security Compliance Checklist
To effectively implement the HIBT compliance checklist, cryptocurrency platforms should align their strategies with the following key components:
1. Regular Security Audits
Like regularly inspecting your home for leaks and weak spots, security audits are essential. Experts recommend conducting audits every quarter to ensure all systems function optimally and vulnerabilities are patched.
2. Data Encryption Practices
Data encryption is akin to locking your valuables in a safe. Encrypting user data protects it from unauthorized access. Techniques such as AES and RSA encryption are standard in securing sensitive information.
3. Identity Verification
Identity verification is essential in authenticating users. Investing in advanced KYC (Know Your Customer) and AML (Anti-Money Laundering) systems not only meets legal requirements but also minimizes fraud risks.
4. Incident Response Plan
Having a plan ready for when things go wrong is like having an emergency exit plan. This involves preparing teams for potential security breaches and establishing protocols to contain the damage.
5. Multi-Signature Wallets
Using multi-signature wallets can be a game changer—this security method requires multiple approvals for transactions, significantly enhancing security.
The Vietnamese Market: A Growing Landscape for Crypto
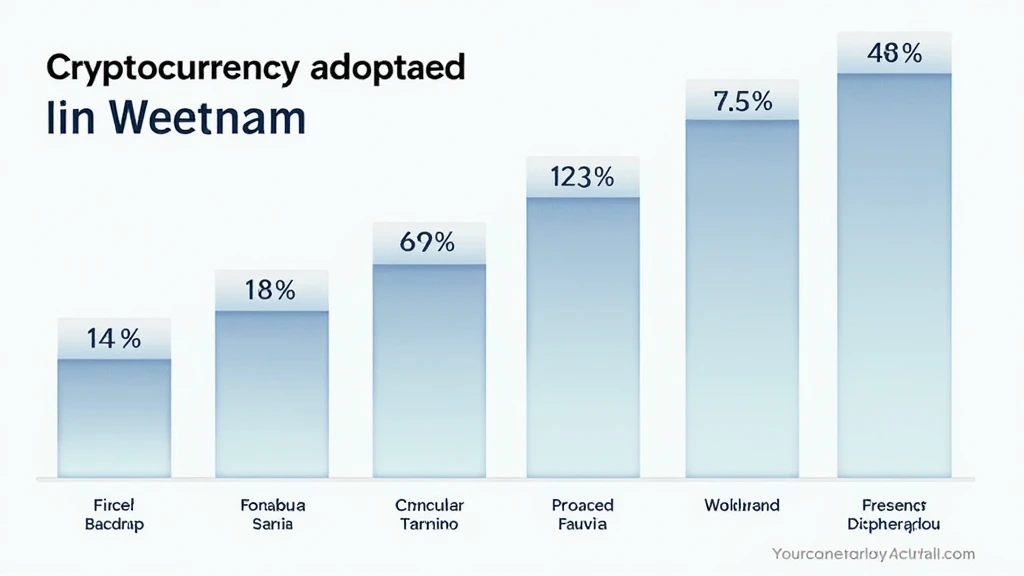
Vietnam is witnessing a meteoric rise in cryptocurrency users, with a reported growth rate of 37% in 2023 alone. However, this spike also brings significant challenges related to compliance and security. Here’s what platforms need to consider:
- Regulatory Adaptation: Understanding the legal landscape in Vietnam will help crypto platforms operate without issues.
- Educational Outreach: Educating users about the HIBT compliance checklist can bolster security perceptions and user investments.
- Localized Security Measures: Tailoring security practices to local market dynamics can enhance trust and usability—this is where integrating localized terms like tiêu chuẩn an ninh blockchain into user interfaces helps.
Real-World Application Scenario: Implementing HIBT Compliance
Let’s walk through an example scenario of how a cryptocurrency platform, CryptoVN, could implement the HIBT compliance checklist:
- Conduct Initial Risk Assessment: CryptoVN performed a risk assessment to identify and catalog vulnerabilities based on their operational model.
- Set Up Security Audits: They partnered with a leading third-party firm to conduct bi-annual security audits.
- Data Encryption: They adopted AES encryption to protect user data and secure transactions over their platform.
- Develop Incident Response: Established an incident response team to address breaches promptly.
- Educate Users: Launched a user-awareness campaign highlighting the importance of the compliance checklist and security measures.
Through this multidimensional approach, CryptoVN not only fortified its security but also enhanced its credibility in the rapidly growing Vietnamese crypto market.
Conclusion: Prioritizing Security and Compliance
The HIBT crypto security compliance checklist is more than just a tool—it’s a necessity for any cryptocurrency platform aiming for longevity and user trust. With the ever-evolving landscape of blockchain technology and increasing regulatory scrutiny, adhering to security protocols is a non-negotiable aspect of business operations.
As we approach 2025, platforms must be proactive in examining their compliance measures and integrating robust security components to navigate this complex environment effectively. By focusing on fundamental aspects such as regular audits, data encryption, and localized compliance strategies, platforms can not only safeguard their assets but also create a secure ecosystem for their users.
For more insights on enhancing your crypto security framework, be sure to explore HIBT.com for in-depth resources.
With the right measures in place, the cryptocurrency world can transform from a wild frontier into a secure digital asset landscape.
Written by: Dr. John Smith, a blockchain security specialist with over 15 published papers in the field, who has also led audits for prominent crypto projects.