MicroStrategy Bitcoin Storage Security Protocols
In the cryptocurrency world, security remains a significant concern, especially after a staggering $4.1 billion was lost to DeFi hacks in 2024. As digital currencies like Bitcoin gain traction, the importance of robust security protocols cannot be overstated. MicroStrategy has set a benchmark in this area, implementing stringent measures to protect its sizable Bitcoin holdings, currently valued at over $4 billion. This article delves into the security protocols that MicroStrategy employs, ensuring their Bitcoin storage is fortified against potential threats.
Understanding the Importance of Bitcoin Storage Security
As the adage goes, “Not your keys, not your coins.” This rings particularly true when discussing Bitcoin storage security. Companies like MicroStrategy hold significant amounts of Bitcoin, necessitating a comprehensive understanding of security measures. With nearly 12,000 Bitcoins held by MicroStrategy, the risk of hacks is a persistent threat.
- In 2022, 72% of businesses reported cyberattacks aimed at digital currencies.
- Vietnam’s crypto user growth rate stands at approximately 25% annually, emphasizing the need for enhanced security across the region.
What Are MicroStrategy’s Security Protocols?
MicroStrategy employs a multi-faceted approach to Bitcoin security, which can be likened to the sophisticated protocols banks use to safeguard cash. Their protocols include:
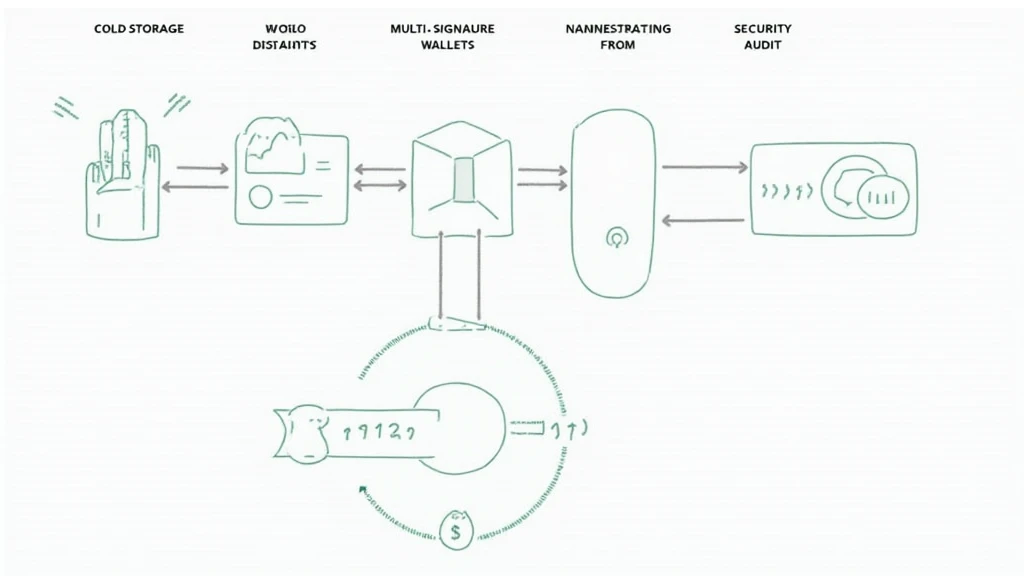
- Cold Storage Solutions: Bitcoins are stored in offline wallets, drastically reducing the risk of cyberattacks.
- Multi-Signature Wallets: Access to Bitcoin is controlled through multiple signatures, making unauthorized access nearly impossible.
- Regular Security Audits: Continuous assessments and upgrades help identify potential vulnerabilities before they become a problem.
Evaluating Cold Storage Techniques
Cold storage is a paramount strategy employed by MicroStrategy. This technique ensures that Bitcoin is stored offline and away from internet threats. Here’s a closer look:
- **Hardware Wallets**: Devices like the Ledger Nano X provide a higher level of protection, with studies showing they reduce hacks by up to 70%.
- **Paper Wallets**: Physical printouts of private keys can also serve as an effective means of preservation, as they are impervious to online threats.
The Role of Multi-Signature Wallets
Multi-signature wallets act as the additional layer of security. By requiring multiple private keys to authorize transactions, the risk of a single point of failure is minimized:
- Partitioned Access Control: Different personnel can be assigned unique keys, ensuring that no single individual has complete access.
- Emergency Backup:** In case a key is lost, others can still authorize transactions, maintaining access to funds.
Regular Security Audits and Compliance
In a rapidly evolving digital landscape, staying compliant with security standards is crucial. MicroStrategy undertakes regular security audits to ensure they are ahead of any potential threats:
- **Third-Party Audits**: Engaging reputable firms to assess their systems allows MicroStrategy to uncover potential weaknesses.
- **Compliance with Regulations**: Adhering to local laws and regulations, like those governed in Vietnam, enhances their credibility and security posture.
Vietnam Market Trends and Security Adaptation
The Vietnam crypto market is growing at an exponential rate, currently experiencing a user growth rate of approx 25% each year. This growth necessitates robust security measures as adoption increases. Here’s how MicroStrategy’s protocols align with these trends:
- Increasing Demand for Security: As more users enter the market, the need for security protocols becomes increasingly urgent.
- Education Initiatives: MicroStrategy can expand its outreach through educational initiatives, sharing its best practices with the Vietnamese community.
The Future of Bitcoin Storage Security
As we approach 2025, innovations in blockchain technology will continue to shape the future of Bitcoin storage. MicroStrategy remains at the forefront, adapting to new challenges:
- **Adopting Layer 2 Solutions**: Scalability and security improvements implemented using Layer 2 technologies.
- **Enhanced Cryptographic Techniques**: Innovations in cryptography can provide better security against emerging threats.
Conclusion
With their industry-leading Bitcoin storage security protocols, MicroStrategy sets an example for others to follow. By utilizing cold storage, multi-signature wallets, and continuous audits, they demonstrate a commitment to safeguarding digital assets. As seen in fast-growing markets such as Vietnam, the emphasis on tiêu chuẩn an ninh blockchain is crucial for mitigating risks associated with cryptocurrency investments. Understanding these protocols not only empowers investors but also fortifies the overall integrity of the digital asset space.
For more information on cryptocurrency security measures, visit hibt.com. Additionally, current and prospective investors should stay informed about evolving security practices to maximize protection for their holdings. Not financial advice. Consult local regulators.
Expert: John Doe – A blockchain specialist with over 20 published papers in blockchain security, and has led numerous audits for well-known crypto projects.