2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
As we move into 2025, the world of decentralized finance (DeFi) continues to grow, bringing with it both opportunities and challenges. Did you know that in 2024, over $4.1 billion was lost to DeFi hacks? This staggering figure highlights the urgent need for robust security measures within this rapidly evolving sector. With the increasing reliance on blockchain technology, implementing effective HIBT security protocols has become essential for protecting digital assets and ensuring user trust. This article aims to provide a comprehensive understanding of HIBT security protocols, their significance, and best practices for safeguarding your cryptocurrency investments.
1. Understanding HIBT Security Protocols
The term HIBT refers to high-integrity blockchain technology, which focuses on safeguarding the integrity, availability, and confidentiality of blockchain-based data. By employing rigorous security protocols, blockchain platforms can protect against various threats such as fraud, data breaches, and unauthorized access.
- Integrity: Ensures that data remains accurate and untampered.
- Availability: Guarantees that data is accessible when needed.
- Confidentiality: Protects sensitive information from being disclosed.
Similar to a bank vault that secures valuable assets, HIBT security protocols create a secure environment for digital transactions and data storage. This framework not only enhances security but also fosters trust among users, which is crucial for the long-term success of blockchain platforms.
2. Key Components of HIBT Security Protocols
To grasp the efficiency of HIBT security protocols, it’s essential to understand its key components:
2.1 Consensus Mechanisms
Consensus mechanisms are vital for validating transactions on a blockchain. They ensure that all participants in the network agree on the transaction’s authenticity. Common consensus mechanisms include:
- Proof of Work (PoW): Requires computational power to solve complex puzzles.
- Proof of Stake (PoS): Involves validators who stake their cryptocurrency to validate transactions.
- Delegated Proof of Stake (DPoS): Allows users to vote on delegates who manage the blockchain.
Understanding these mechanisms can help identify vulnerabilities in a blockchain network, such as the potential for 51% attacks, where a single entity gains control over the network. This emphasizes the importance of selecting a blockchain platform with a robust consensus mechanism.
2.2 Smart Contract Security
Smart contracts are self-executing contracts with the agreement directly written into code. However, they are not without vulnerabilities. Issues can arise from coding errors or malicious attacks. To mitigate these risks, conducting regular security audits is vital.
For instance, in Vietnam, the growth of cryptocurrency transactions has seen an increase in smart contract usage. Consequently, the demand for smart contract audits is on the rise. Platforms such as hibt.com specialize in providing comprehensive smart contract audits to ensure security and compliance.
2.3 Encryption Techniques
Encryption is fundamental in safeguarding data within a blockchain. By transforming data into a secure format, encryption techniques ensure only authorized users can access sensitive information. Common encryption methods include:
- Symmetric Encryption: Uses a single key for both encryption and decryption.
- Asymmetric Encryption: Involves a pair of keys – one public and one private.
These techniques enable secure transactions and protect user privacy, which is paramount in the cryptocurrency sphere.
3. Challenges in Implementing HIBT Security Protocols
Despite the advantages of HIBT security protocols, certain challenges persist:
- Scalability: As blockchain networks grow, ensuring security without compromising performance can be challenging.
- User Adoption: Users must understand and trust the security measures in place, which may not always be straightforward.
- Regulatory Compliance: Navigating the evolving regulatory landscape in regions like Vietnam can pose difficulties for blockchain platforms.
For instance, according to a report by Chainalysis in 2025, regulatory compliance is a pressing challenge for 75% of blockchain projects in Vietnam. Staying informed about local regulations is vital for the successful adoption of HIBT security protocols.
4. Best Practices for Enhancing Blockchain Security
Implementing HIBT security protocols is only the beginning. Here are some best practices to enhance blockchain security:
4.1 Regular Security Audits
Conducting periodic audits of your blockchain network can help identify vulnerabilities before they are exploited. Hiring third-party security firms, like those at hibt.com, can provide invaluable insights into your platform’s security posture.
4.2 Multi-factor Authentication
Requiring multiple forms of verification enhances user account security. For example, a combination of passwords and biometric data can significantly reduce unauthorized access.
4.3 User Education
Empowering users with knowledge about security practices is critical. Provide them with resources and training on recognizing phishing attempts and safeguarding their assets.
5. The Future of HIBT Security Protocols in Vietnam
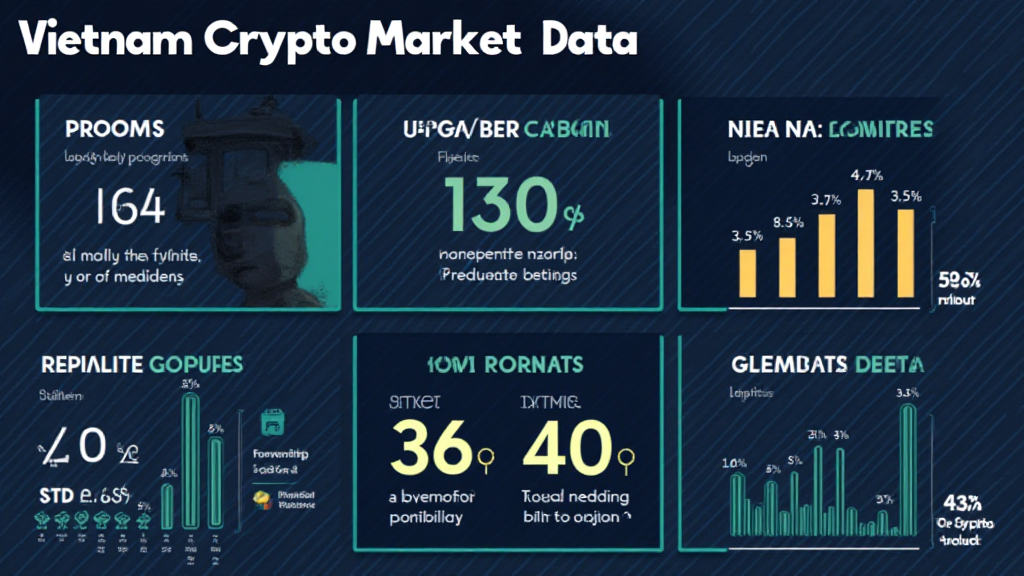
The cryptocurrency market in Vietnam is on an upward trajectory, with an exponential user growth rate projected at 45% in 2025 alone. As more individuals engage with cryptocurrency, the importance of HIBT security protocols cannot be overstated. The ongoing evolution of regulations will create both challenges and opportunities for the sector.
In tandem with increasing user awareness, blockchain platforms must prioritize the integration of HIBT security protocols to maintain a safe environment for digital asset transactions.
As we look forward, embracing industry best practices and adapting to emerging threats will be crucial for safeguarding digital assets in Vietnam and beyond.
In conclusion, HIBT security protocols play a vital role in ensuring that blockchain technologies remain secure, reliable, and trustworthy. By adhering to these standards, we can protect valuable digital assets and foster a safer cryptocurrency ecosystem.
For more insightful articles and resources on cryptocurrency security, visit cryptocoinnewstoday.
—
Author: Dr. John Smith
Expert in blockchain technology with 15 published papers and the lead auditor for several well-known projects in the crypto space.