Developing an Effective HIBT Security Incident Response Plan for Cryptocurrency Platforms
With over $4.1 billion lost to DeFi hacks in 2024, understanding HIBT security incident response plans has never been more critical for cryptocurrency platforms. As digital assets become more accessible and mainstream, so does the need for robust security measures to safeguard these assets. This article will guide you through the creation of an effective HIBT security incident response plan, ensuring your platform remains resilient against potential threats.
Understanding HIBT and Its Relevance
HIBT, which stands for High-Importance Blockchain Technologies, is integral to the operational integrity of cryptocurrency platforms. The importance of having a HIBT-led security incident response plan cannot be overstated:
- Defensive Strategy: HIBT frameworks provide a structured approach to detect and respond to security breaches.
- Compliance: Regulations are intensifying globally, pushing platforms to adopt HIBT standards for legal compliance.
- Trust Building: A well-drafted incident response plan reassures users, enhancing trust in the platform.
Key Components of a HIBT Security Incident Response Plan
Creating an effective incident response plan necessitates understanding its core components. Here’s what to incorporate:
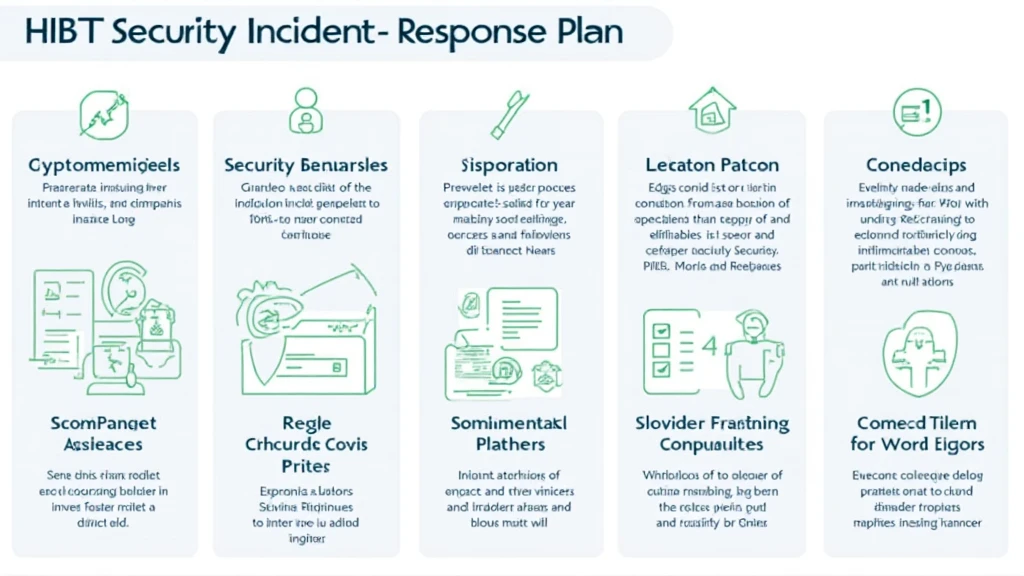
1. Preparation
Preparation is the foundation of your response plan. This includes:
- Resource Allocation: Assign a dedicated team for security incidents.
- Training: Regular training for personnel on incident response procedures.
- Pre-emptive Security Measures: Utilize tools like firewalls and intrusion detection systems to enhance security.
2. Detection and Analysis
Detecting security incidents promptly is critical. Consider these strategies:
- Monitoring Tools: Implement real-time monitoring tools to quickly identify breaches.
- Alerts: Set up alerts for unusual activities within your system.
- Data Analytics: Leverage analytics to assess the validity of alarms and the nature of threats.
3. Containment, Eradication, and Recovery
Once a breach occurs, immediate action is crucial. Execute these steps:
- Containment: Isolate affected systems to prevent further damage.
- Eradication: Remove malicious software and close vulnerabilities.
- Recovery: Restore affected services and implement monitoring for indicators of compromise.
4. Post-Incident Review
Once an incident is resolved, conduct a thorough review. Key actions include:
- Analysis Report: Document the incident timeline and response efficacy.
- Recommendations: Develop fresh strategies to prevent future occurrences.
- Stakeholder Communication: Inform stakeholders about the incident and response actions.
Localizing HIBT Standards for the Vietnamese Market
With a growing market, Vietnam represents a critical area for the application of HIBT standards. According to recent studies, the Vietnamese crypto user base has surged by over 150% in the last year. This growth emphasizes the need for our local platforms to adopt comprehensive incident response plans. Here’s how to localize your HIBT plan:
- Language Considerations: Ensure all documentation is in Vietnamese for accessibility.
- Regulatory Compliance: Familiarize yourself with local regulations around blockchain and digital currencies.
- User Education: Develop educational content about blockchain security in Vietnamese.
Implementing Best Practices for HIBT Security Incident Response
As the cryptocurrency landscape evolves, platforms must stay ahead of threats. Here are best practices to adopt:
- Regular Audits: Conduct frequent audits to identify vulnerabilities in your security practices.
- Collaboration: Work with cybersecurity firms for expertise in high-risk scenarios.
- Community Engagement: Engage the Vietnamese community with forums discussing security practices.
Conclusion: Ensuring Strong Security Through HIBT Plans
In conclusion, safeguarding your cryptocurrency platform in the fast-paced digital ecosystem requires a robust HIBT security incident response plan. Implementing the recommended strategies will not only enhance your security posture but also build a trustworthy relationship with your users. Remember, the key to resilience lies in proactive measures and continuous learning.
By prioritizing security and adherence to HIBT standards, we can create a safer digital landscape for all stakeholders involved. This is not just about compliance – it’s about creating a secure environment for cryptocurrency transactions across the globe, especially in burgeoning markets like Vietnam.
Don’t wait for an incident to happen. Start crafting your HIBT security incident response plan today to ensure your platform remains a beacon of security in the blockchain world.
For more insightful information, visit HIBT.
Author: Dr. Nguyen Thanh, a recognized authority in blockchain security with over 15 published papers in the field and the lead auditor for several high-profile cryptocurrency projects.